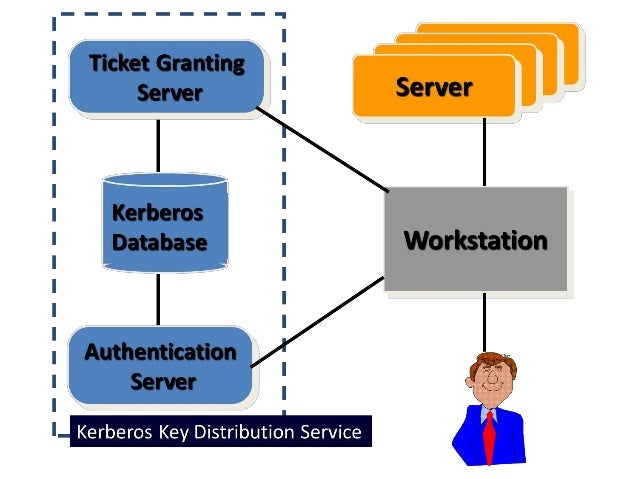
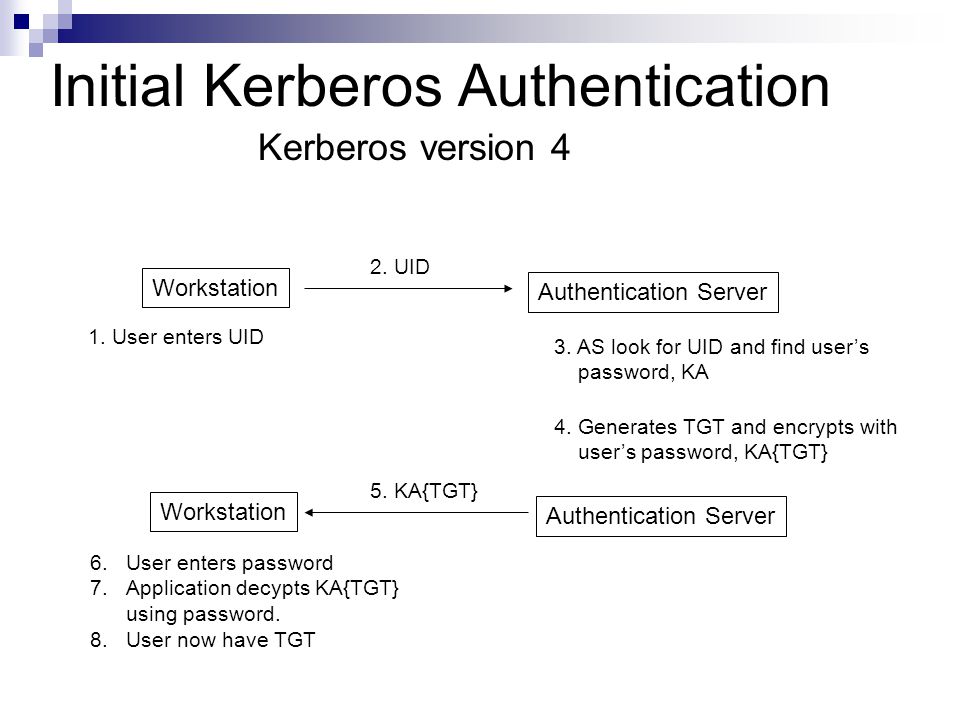
Kerberos Authentication Protocol

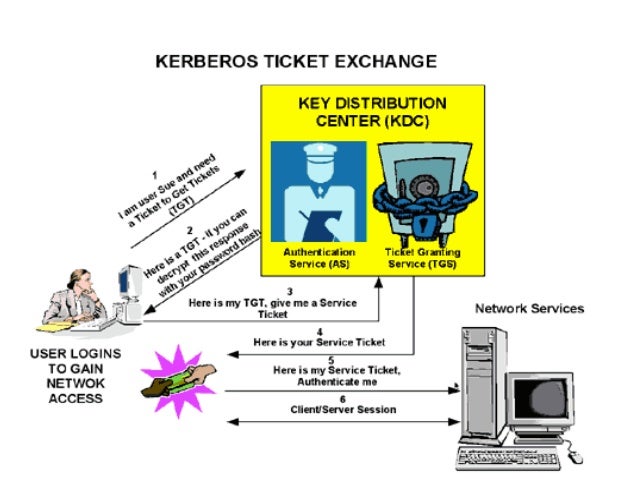
Five Steps To Using The Kerberos Protocol
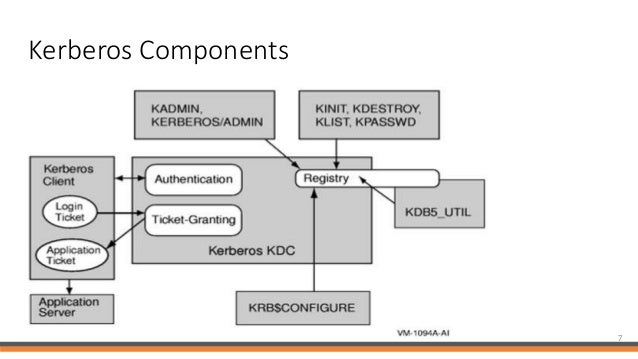
Kerberos For Distributed System Security Omal Perera

The Authentication Service Kerberos And It S Limitations Ppt Download

1 Cryptography Css 329 Lecture 12 Kerberos 2 Lecture Outline Kerberos Overview V4 V5 Ppt Download

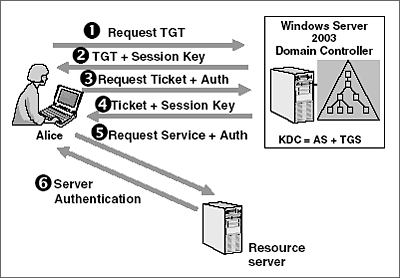
Active Directory Authentication Methods How Do Kerberos And Ntlm Work Learn Solve It

Kerberos Authentication Protocol

Idm In Banking Industry Banking Industry Banking Development

Kerberos Protocol Software Development Math Development
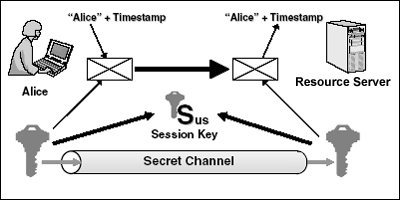
Five Steps To Using The Kerberos Protocol

Using Certificates For Aadj Onpremises Singlesign On Single Sign In 2020 Certificate Templates Certificate Of Recognition Template Certificate Of Achievement Template